Another problem I had recently asked about, had been a failed iPhone MDM rollout. As in my previous blog post mentioned, the endpoints in the environment – including iPhones – are managed with Microsoft Endpoint Manager. During one of the iPhone deployments, the user received the error Guided Access app unavailable. Please contact your administrator (in German: Die App "Geführter Zugriff" is nicht verfügbar. Wenden Sie sich an Ihren Administrator.) in iOS after he had logged in with his account to the Intune Company Portal app.
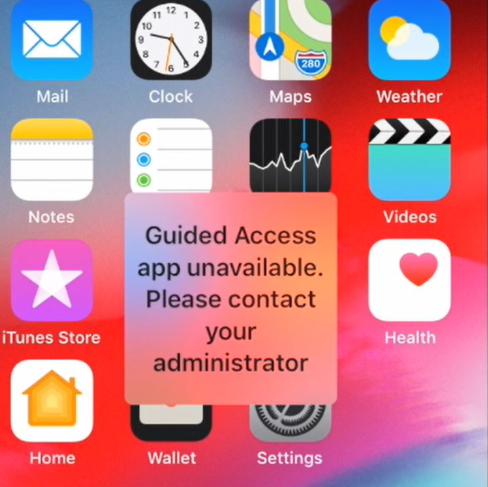
Guided Access app unavailable. in iOSAfter having logged in the first time into his account through Company Portal app, the iPhone is automatically registered in the connected Azure AD and will appear in Microsoft Endpoint Manager.
Nevertheless, the error did not go away.
Checking the usual suspects
As I had been on the phone and tasked with other things, I suggested to work off the following list:
Verify GSM/LTE internet connection
First of, I checked the availability of the GSM/LTE connection in addition to the WLAN connection. It might be that there is some trivial network connectivity issue.
We already had the case that the WLAN connection were available but the mobile network had not been. This lead also to the error above. From a technical point of view I am not sure why that happens.
Just wait a few minutes
As stupid as it sounds, the error could be gone after a few minutes. I waited for 15 minutes: The startup process of Intune’s iOS app deployment can take a little bit. In addition to that, we had already the issue that the Apple services were down.
Wipe and remove the device from Microsoft Endpoint Manager
After 15 minutes I wiped the smartphone through Microsoft Endpoint Manager, removed the device from the user in Azure AD and then gave it another try. It also did not work.
Digging deeper
As the previous solutions did not work, I took a deeper look into it.
Check for an expired VPP token
When googling for the error message with the keywords intune and/or endpoint protection manager, you probably will find the article iOS or iPadOS device is stuck on an enrollment screen with the section Determine if there’s something wrong with the VPP token. We had been burned by this issue a few months ago, so I were pretty sure that it did not was the reason for our problems. Indeed, the token were valid.
Analyzing the iPhone’s system state
As always, when I am debugging a system, I collected all available information:
- In Apple Business Manager, the iPhone had been successfully registered. Otherwise, no deployment of Intune could have happened: During the first start of the iPhone, iOS checks if the serial number is available in the ABM and if yes, it forwards the roll-out process to Microsoft Endpoint Protection Manager.
- The connection from iOS to Microsoft Endpoint Protection Manager / Intune did also work: The Company Portal app got installed and the user were able to log in.
- After the user logged in the Company Portal app, the iPhone showed up in Intune and -inevitably- Azure AD.
- Other iPhone devices had contacted Intune during the time of analysis. So there were probably no issues with Intune itself.
All in all, this must have been some configuration issues on our side. I opened up an existing and already working iPhone in Microsoft Endpoint Manager and compared it to the new, not-working iPhone.
I stumbled upon the fact, that the erroneous iPhone were not encrypted:
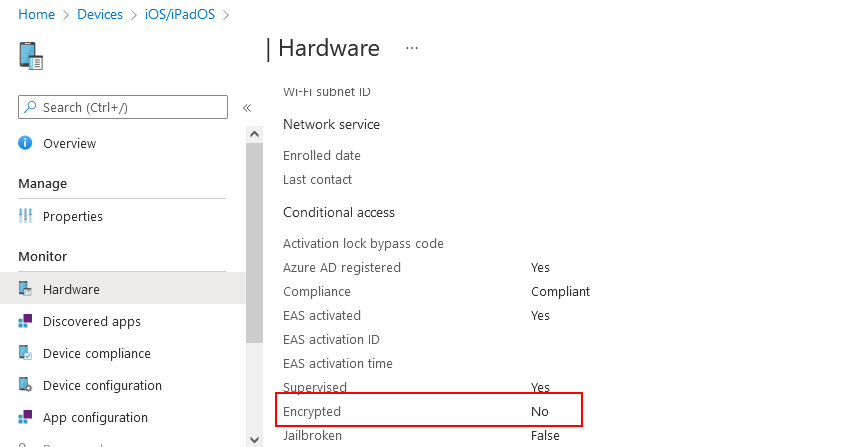
This should definitely not be the case, as we are requiring all smartphones to be encrypted. The user had also entered a PIN for device encryption.
As I headed over to the Device compliance tab, the Built-in Device Compliance Policy showed an error for the setting Has a compliance policy assigned with the error code 0xfde9:
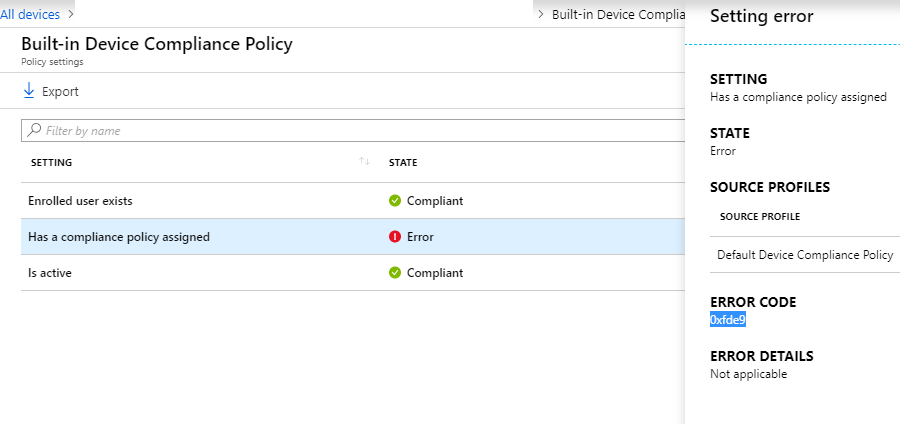
The error code 0xfde9 in our context basically meant: “Hey, your iPhone is known to us and we let it know into our Azure AD. But sorry, we don’t know what policy to enroll for that device”.
In our case, we have two Device compliance policies: one for Android smartphones and one for iPhones. Both Device compliance policies are basically assigned to the device, after a user had been logged to the device (which worked) and if the user belongs to one of two included security groups.
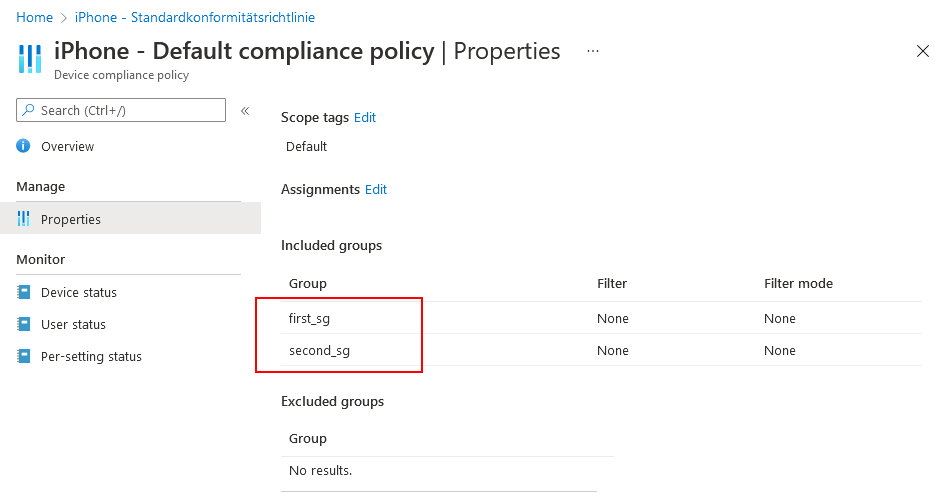
The two security groups do have a dynamic membership, based upon the user’s Azure AD Company Name field.
You might already have guessed it: The user with the erroneous had no valid Company Name field content and so did not belong to any included security group (first_sg or second_sg). Without any proper security group, Intune were not been able to assign a compliance policy.
I updated the user’s Company Name field, waited a few minutes and then wiped the iPhone again. With the next user’s login to the Company Portal app, everything worked as expected.